Part I: 100k Emails that Shaped the Early Internet
Exploring the Cypherpunks – pioneers who championed cryptography and open standards during the internet's formative years.
This Part I explores the history of the Crypto Wars – how battles over encryption shaped early technology adoption and regulation in the 1990s. Part II looks at current investment opportunities in companies leveraging the new, open standards that will come to power autonomous software.
01 | Decoding the emails that shaped the internet
At Timespan, we study historical patterns to anticipate how technology will evolve.
The Crypto Wars of the 1990s offer a fascinating lens into how transformative technologies emerge despite regulatory resistance. (Note: “Crypto” here refers to cryptography, not cryptocurrency.)
Strong cryptography – the mathematical practice of encoding information for privacy – became the foundation of our modern digital economy. Without it, the basic operations we take for granted would be impossible: online banking, e-commerce, secure messaging, digital signatures, and virtually every sensitive online interaction.
In the early 1990s, the U.S. government classified strong encryption as a “munition” under arms trafficking laws, effectively making it illegal to export this technology outside the U.S. This classification threatened to splinter the emerging internet into a two-tier system: weak encryption for international users and strong encryption for domestic ones.
Enter the Cypherpunks – a group of technologists, mathematicians, and privacy advocates who believed privacy and encryption were fundamental rights in the digital age. Notable Cypherpunks include Hal Finney, Adam Back, Julian Assange, Marc Andreessen and (possibly) Satoshi Nakamoto.
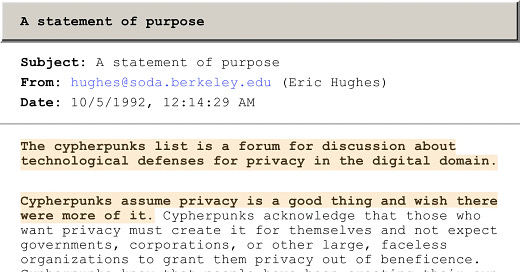
ID: <9210050721.AA01865@soda.berkeley.edu>[1]
From 1992 to 1998, over 100,000 messages were exchanged across a range of topics on the Cypherpunk listserve. A decade ago someone preserved these emails in eight raw text files[2] that were unstructured and difficult to read.
To make these emails accessible, I used custom parsing algorithms to transform the raw text files into an interactive digital archive:
These archives serve as a unique, digital time capsule of the movement that was the precursor to the modern internet. We have the opportunity to study these archives and derive valuable insights into patterns of technology adoption during periods of significant innovation.
In Part I of this blog post we’ll dig into the history and context of the Crypto Wars, particularly around technology adoption cycles. Part II will break down how we apply the learnings from the past to identify investment opportunities today.
02 | Major technology transformations coalesce around open standards
Early Cypherpunk emails underscore a timeless principle — new technology requires open, shared frameworks to facilitate developer collaboration and achieve widespread adoption.
The evolution of two different encryption standards – RSA and PGP – reinforces this concept.
Developed in 1977, the RSA standard (named after its creators Rivest-Shamir-Adleman), marked a breakthrough in public key cryptography. It introduced a method for secure data transmission over public networks, laying the groundwork for encrypted communication over the internet.
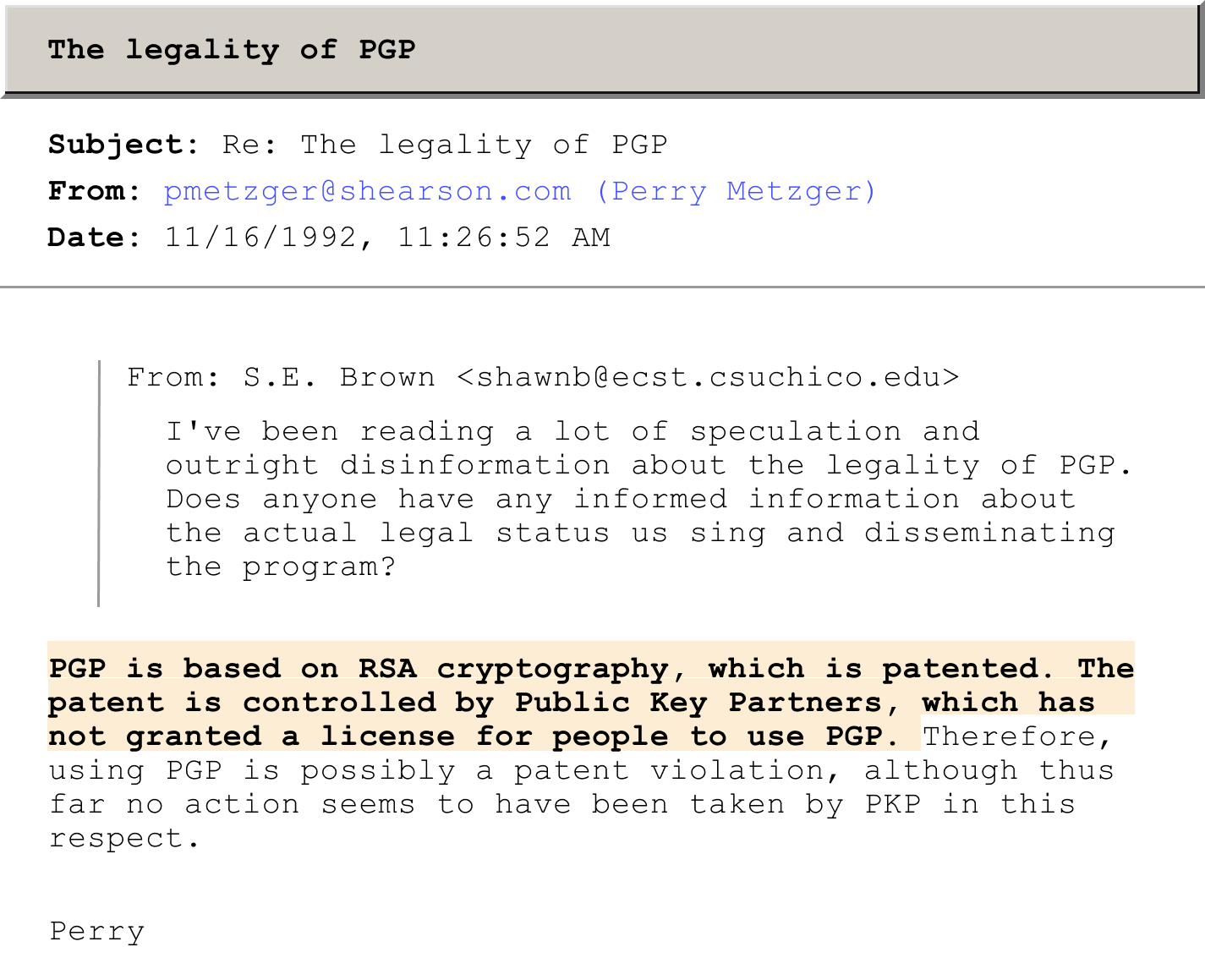
However, RSA’s initial patent restricted the technology’s widespread use, limiting adoption.
In contrast, PGP (Pretty Good Privacy), created by Phil Zimmermann in 1991, democratized encryption by offering an unlicensed, freely available implementation of RSA. Zimmermann published PGP’s source code online, giving anyone the ability to encrypt their emails, files, and messages.
ID: <9211161902.AA08397@newsu.shearson.com>
The openness of PGP was the catalyst needed to fuel rapid adoption of the RSA cryptography standards.
The tension between RSA and PGP was frequently discussed on the Cypherpunk listserv, and there was general consensus that foundational technology breakthroughs only become useful if they are open and accessible.
ID:<2.2.32.19960409153328.0075c2c0@panix.com>
The Cypherpunks championed cryptography and encryption not for secrecy, but as a trusted tool for securely sharing private information – like credit card data – which was essential to the new digital economy.
They pushed back against U.S. policy, which made it illegal to export strong encryption overseas. For them, these bans hindered the growth of the internet and hurt U.S. global competitiveness.
ID:<199409220341.UAA02254@jobe.shell.portal.com>
The Cypherpunks, as the early advocates and builders of encryption, emphasized distribution and championed this technology as a fundamental right, likening it to public infrastructure – open, essential, and unstoppable.
03 | How openness outpaces regulation and drives economic growth
Until 1996 sending strong encryption overseas was considered a federal crime, the equivalent of exporting weapons to foreign adversaries.
This became the foundational issue of the Crypto Wars.
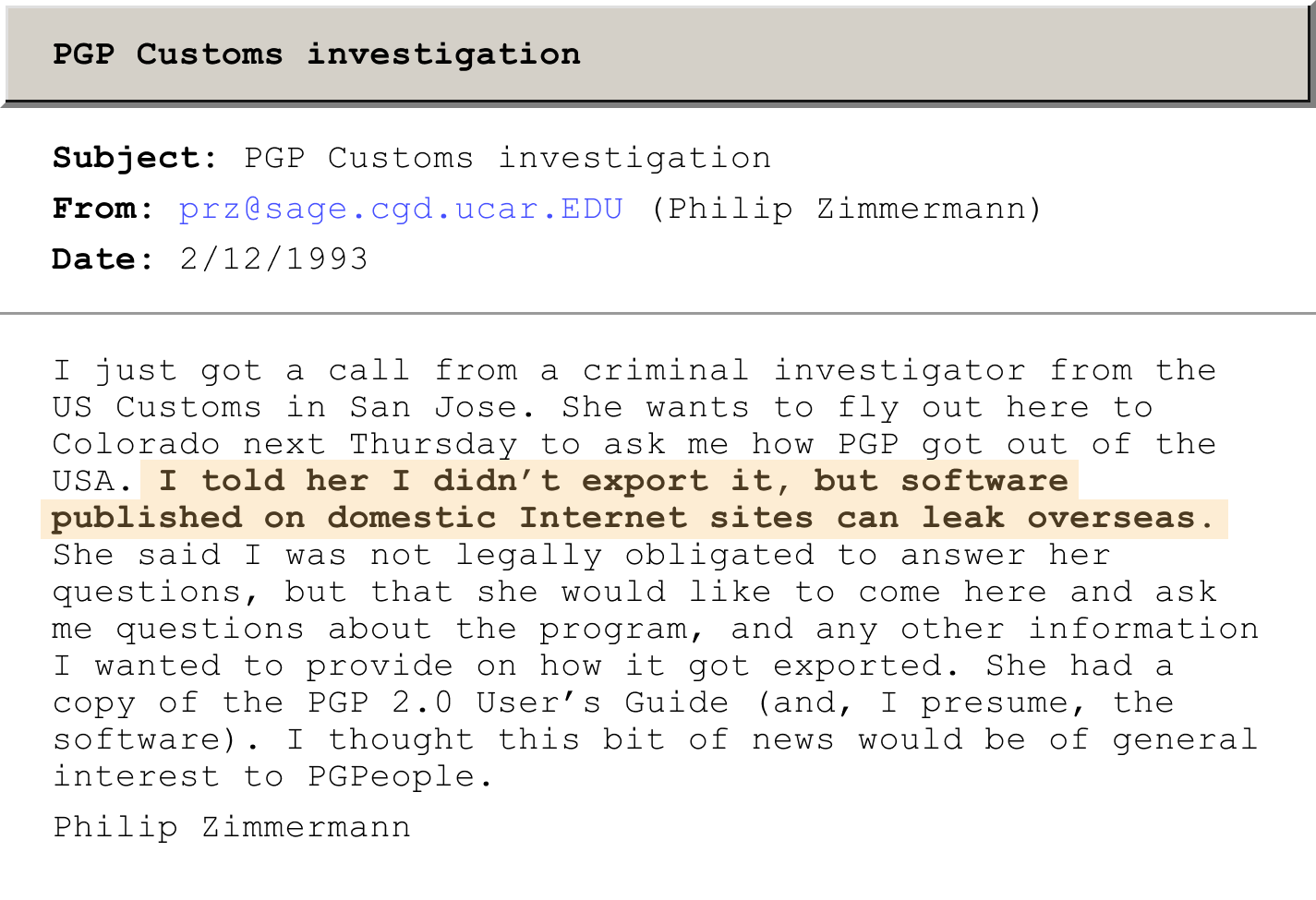
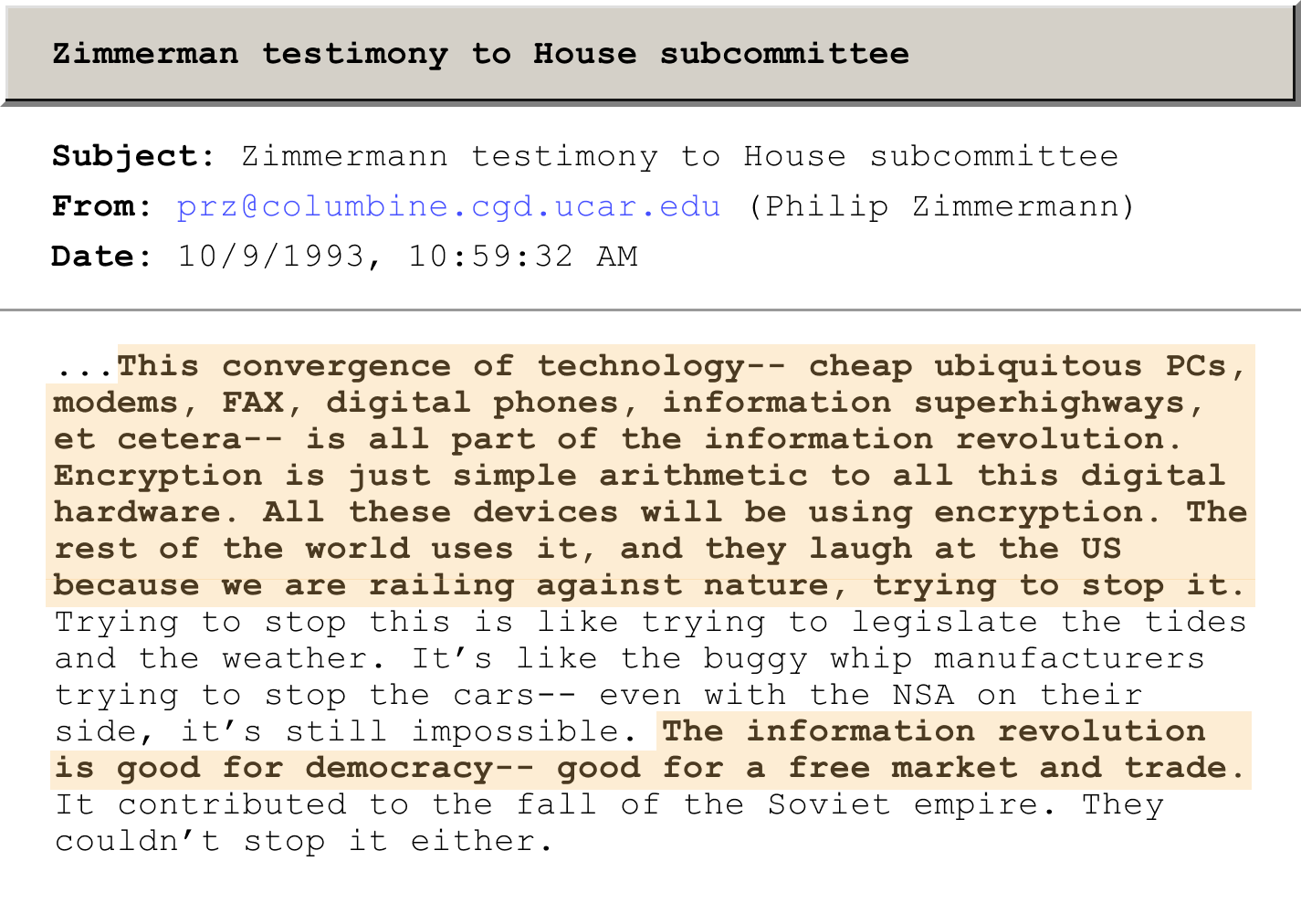
Phil Zimmermann became a central figure in this battle when he released his open-source version of PGP in 1991 and was accused by U.S. officials of violating federal law.[3]
ID: <9302132122.AA13118@nexsys.nexsys.net>
Zimmerman and associates, including many from the Cypherpunk community, were subject to a 3-year investigation that included subpoenas, Senate hearings, and threats of jail time.
However, by 1993, the U.S. policy of regulating encryption as a weapon began to unravel, given the rapid adoption of open encryption globally.
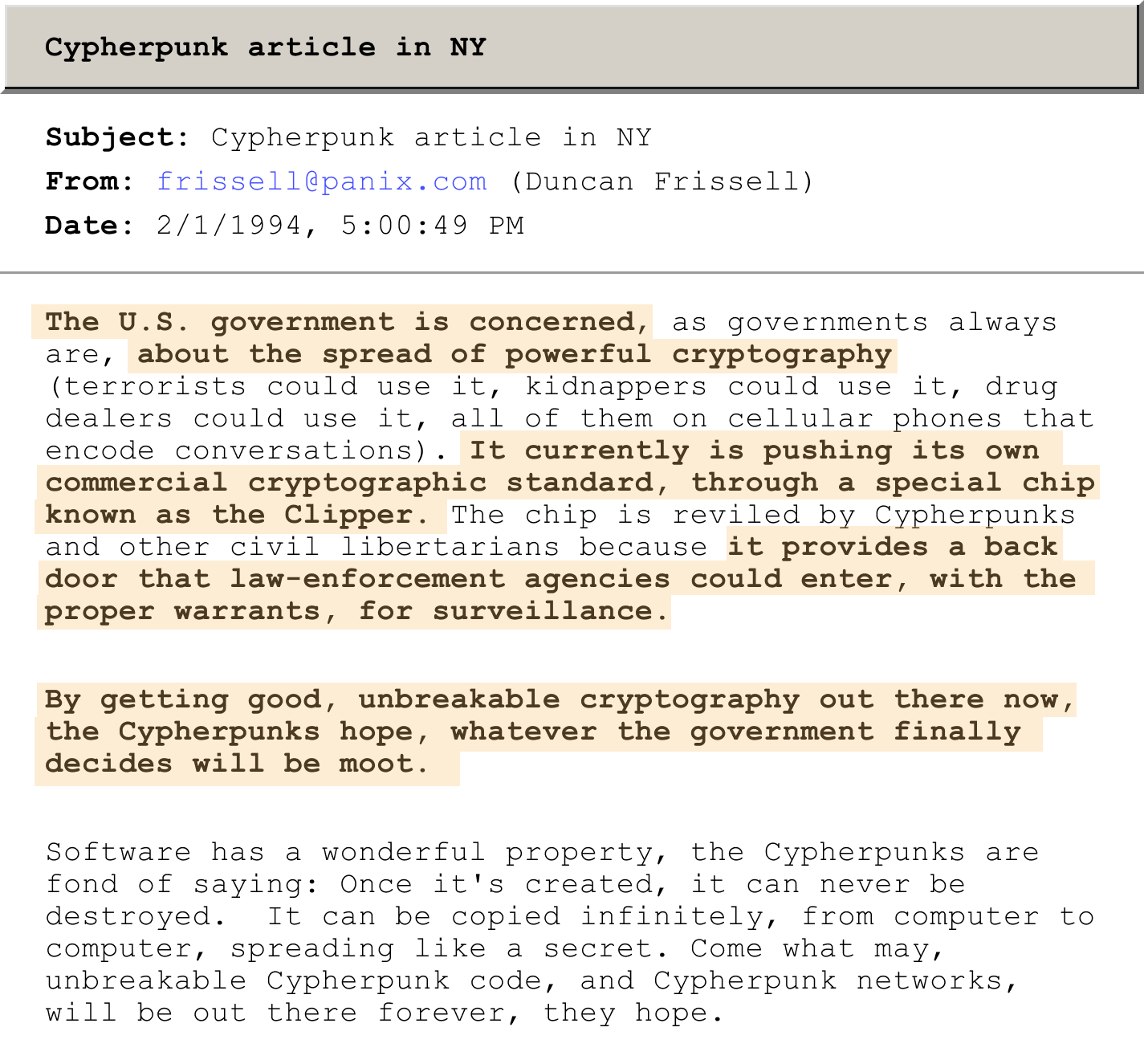
The Clinton administration made a few final attempts to control this technology. First, through a massive PR campaign, portraying encryption and cryptography as a tool for, “pornography, terrorists, tax evaders, and criminals.[4] Second, through a centralized alternative. The U.S. government announced the Clipper Chip initiative, a public-private partnership between the NSA and AT&T, where chips in AT&T’s devices would use cryptography co-developed with the NSA, giving the government “back door” access to private communication.[5]
The Clipper Chip initiative never took off, and by the mid-1990s, the Cypherpunks had won the Crypto Wars in the court of public opinion.
In 1996, President Clinton signed Executive Order 13026, which shifted the regulatory framework of commercial encryption from munitions to commerce. The investigation into Zimmerman was dropped, and export controls on encryption were dismantled.[6]
This history shows – new technology, especially when cheap and widely accessible, does not conform to policy frameworks that try to suppress or control.
Regulatory attempts to limit or slow new innovation ultimately hurts domestic economic interests, and over time governments are forced to change these policies as the consequences become too significant to avoid.
ID: <9310091757.AA04856@columbine.cgd.ucar.EDU>
While U.S. policymakers focused on regulating cryptography as a weapon that could be used for criminal activities, the Cypherpunks knew cryptography was needed in order to unlock new markets on the internet – e-commerce, email, cloud computing, data storage, and more.
This lesson – that open-source, foundational technologies typically outpace regulation and centralized alternatives – is relevant today.
When new innovations provide solutions that are better-faster-cheaper, they drive mainstream adoption, making it prudent for governments and businesses to adapt, rather than suppress.
04 | Cypherpunk cypherbites
While the Cypherpunks were pioneering internet privacy, their mailing list wasn't all cryptographic algorithms and policy debates – the archives reveal the Cypherpunks were just like us.
Here are some cherry picked emails for your amusement.
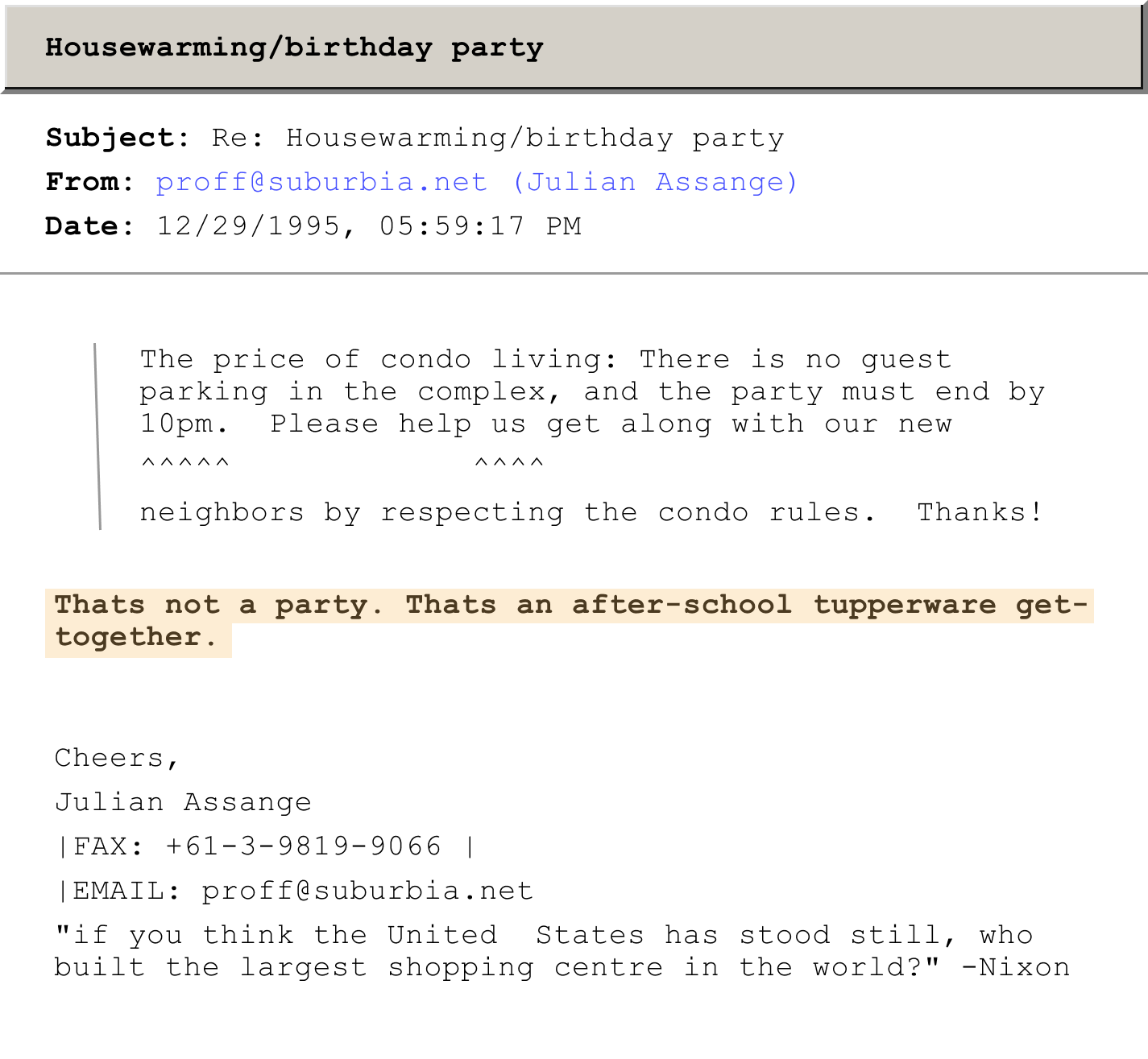
Julian Assange is very particular about his parties
ID:<199512300046.LAA16884@suburbia.net>
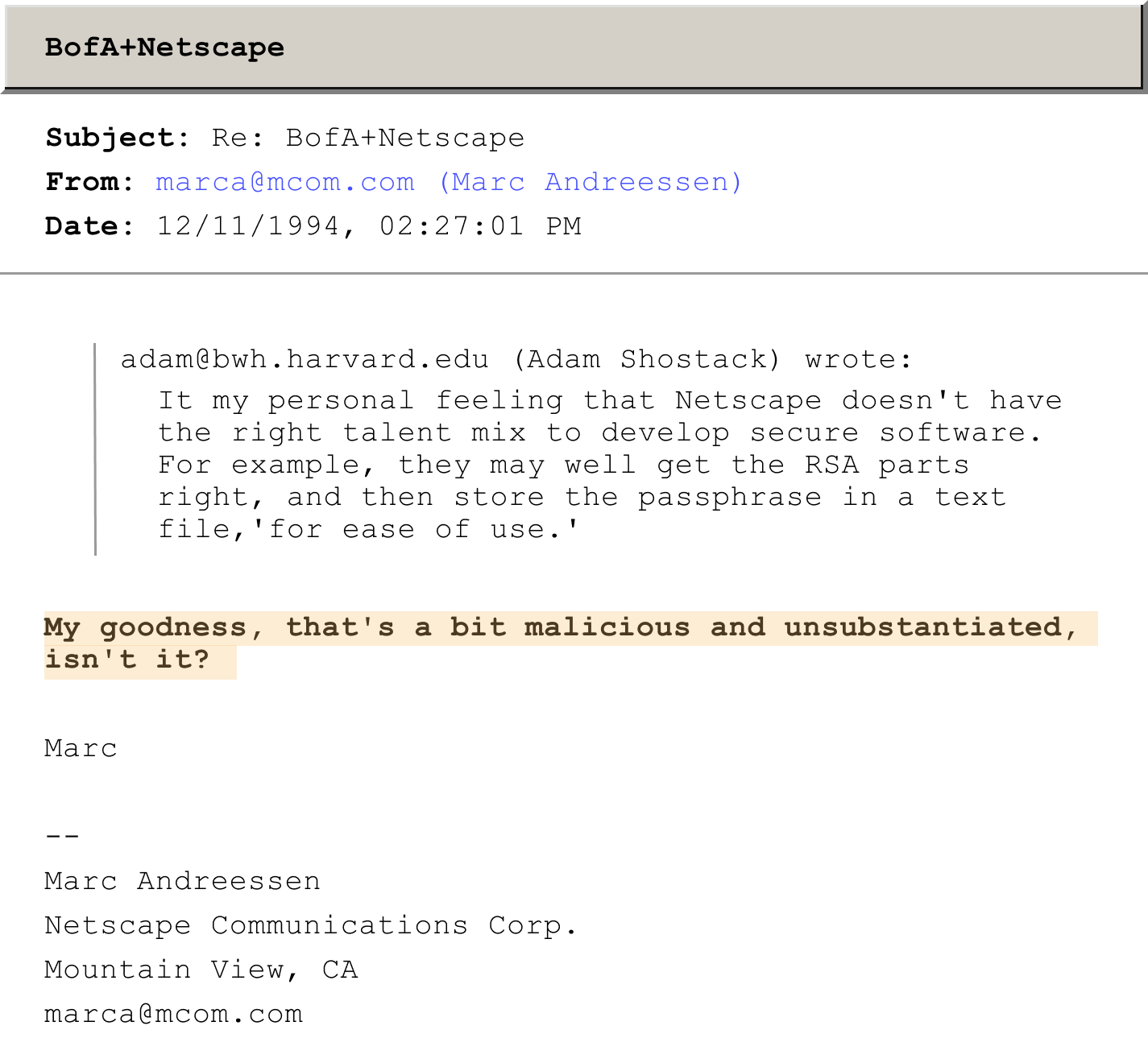
Marc Andreessen was responding to internet trolls back in 1994
ID: <199412112227.WAA23971@neon.mcom.com>
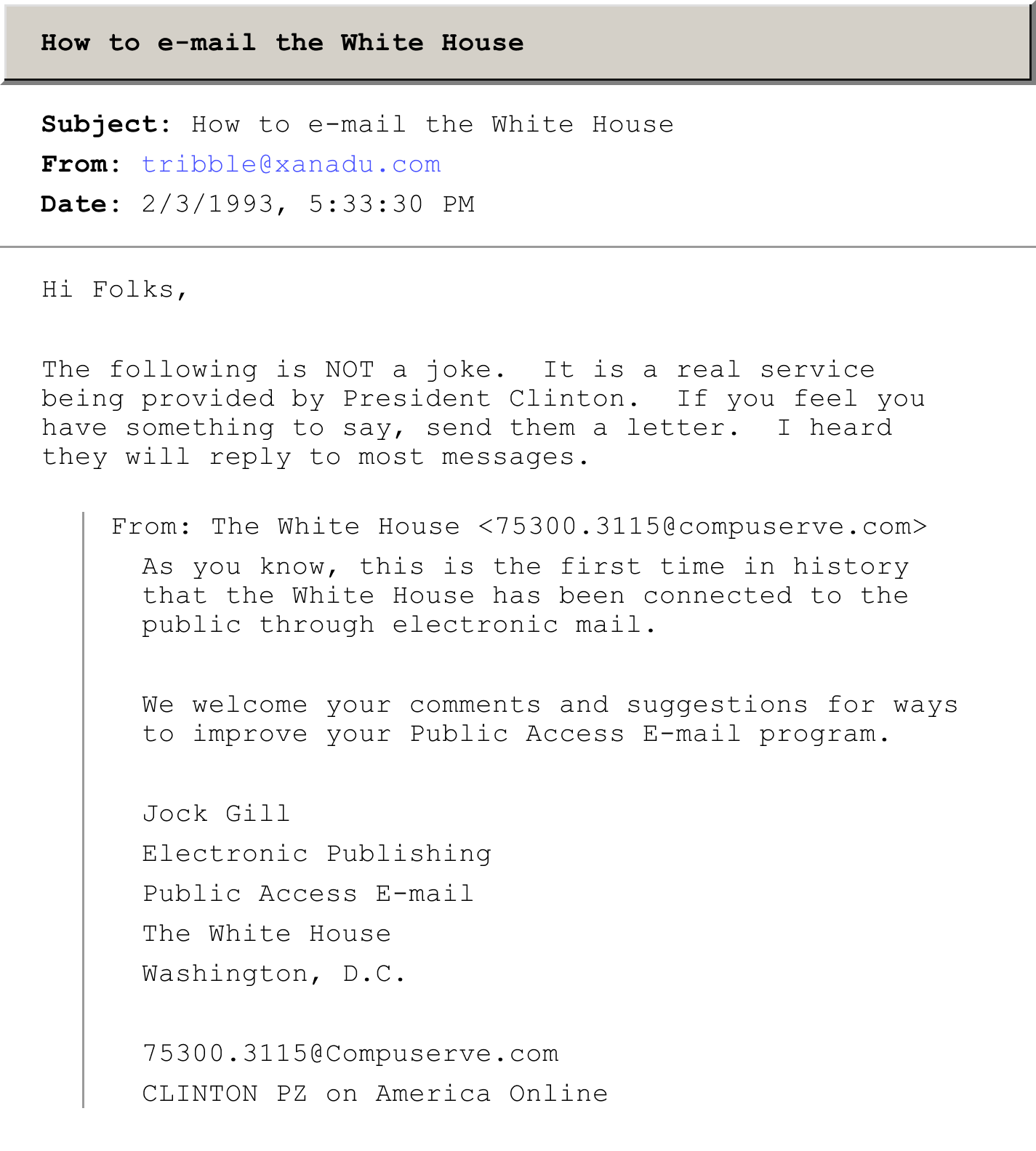
Clinton’s first email address: 75300.3115@compuserve.com
ID: <9302032358.AA00498@xanadu.xanadu.com>
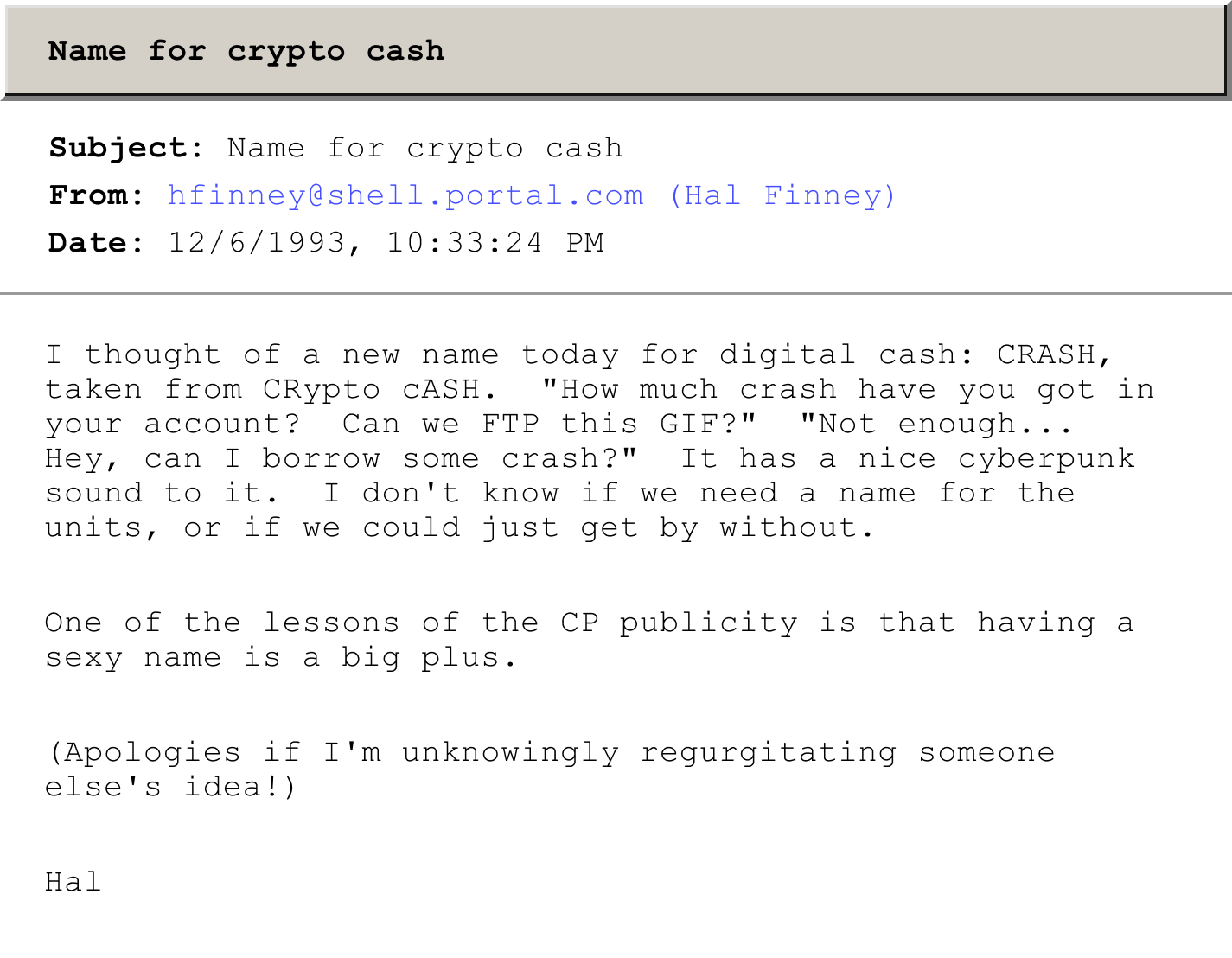
Bitcoin was almost named CRASH
ID: <9312070630.AA28857@jobe.shell.portal.com>
Sung to the tune of “Santa Claus is Coming to Town”
ID: <199712251031.LAA09046@basement.replay.com>
Please explore the Cypherpunk archives and let me know what you discover!
email: maaria@timespan.vc || twitter: @maariabajwa || linkedin: @maariab || github: @iloveburritos
I’ll repost my favorite replies.
Endnotes:
[1] To read a message in its entirety, search “ID: <9210050721.AA01865@soda.berkeley.edu>” in the search box on https://cypherpunk.timespan.vc/
[2] https://cypherpunks.venona.com/date/
[3] A recent appeals court decision ruled OFAC sanctions against privacy protocol Tornado Cash were unlawful because open source code and immutable smart contracts cannot be considered legal property because they are not capable of being owned. While these legal decisions will take many years to finalize, they are indicators of the changing regulatory landscape in a technology market that is changing rapidly. https://storage.courtlistener.com/recap/gov.uscourts.txwd.1211705/gov.uscourts.txwd.1211705.99.0.pdf
[4] More recently we have seen similar claims made against cryptocurrencies and blockchain technology. "At a hearing of the Senate Banking, Housing, and Urban Affairs Committee, U.S. Senator Elizabeth Warren (D-Mass.) called out crypto’s use by terrorists, ransomware gangs, drug dealers, and rogue states to launder funds." https://www.warren.senate.gov/newsroom/press-releases/icymi-at-hearing-warren-warns-about-cryptos-use-for-money-laundering-by-rogue-states-terrorists-and-criminals
[5] The UK government recently ordered Apple to create a back door allowing them to retrieve all encrypted cloud content, for users around the world. This order would apply to users who have opted into Apple’s end-to-end encrypted cloud service. https://www.washingtonpost.com/technology/2025/02/07/apple-encryption-backdoor-uk/
[6] https://www.govinfo.gov/content/pkg/WCPD-1996-11-18/pdf/WCPD-1996-11-18-Pg2399.pdf